

Networking Demands Soar
Navigating the Post-Pandemic Office Landscape. Discover how we meet the rising networking demands of modern business environments. Stay connected and competitive with our cutting-edge solutions.


Old School Cyber Attacks
Old School Cyber Attacks: A 2023 Analysis of Timeless Threats In the world of cybersecurity, new threats and attack techniques continuously emerge, capturing the attention[...]


The Problem With Cybersecurity: People!
The Problem With Cybersecurity: People – Unveiling the Human Factor in Data Breaches Cybersecurity is a complex and ever-evolving field, with new threats and challenges[...]


Hellokitty Ransomware Code Leaked
Hellokitty Ransomware Code Leaked: Urgent Security Update Needed The HelloKitty ransomware, a notorious strain of malware that emerged in 2020, has recently made headlines again.[...]
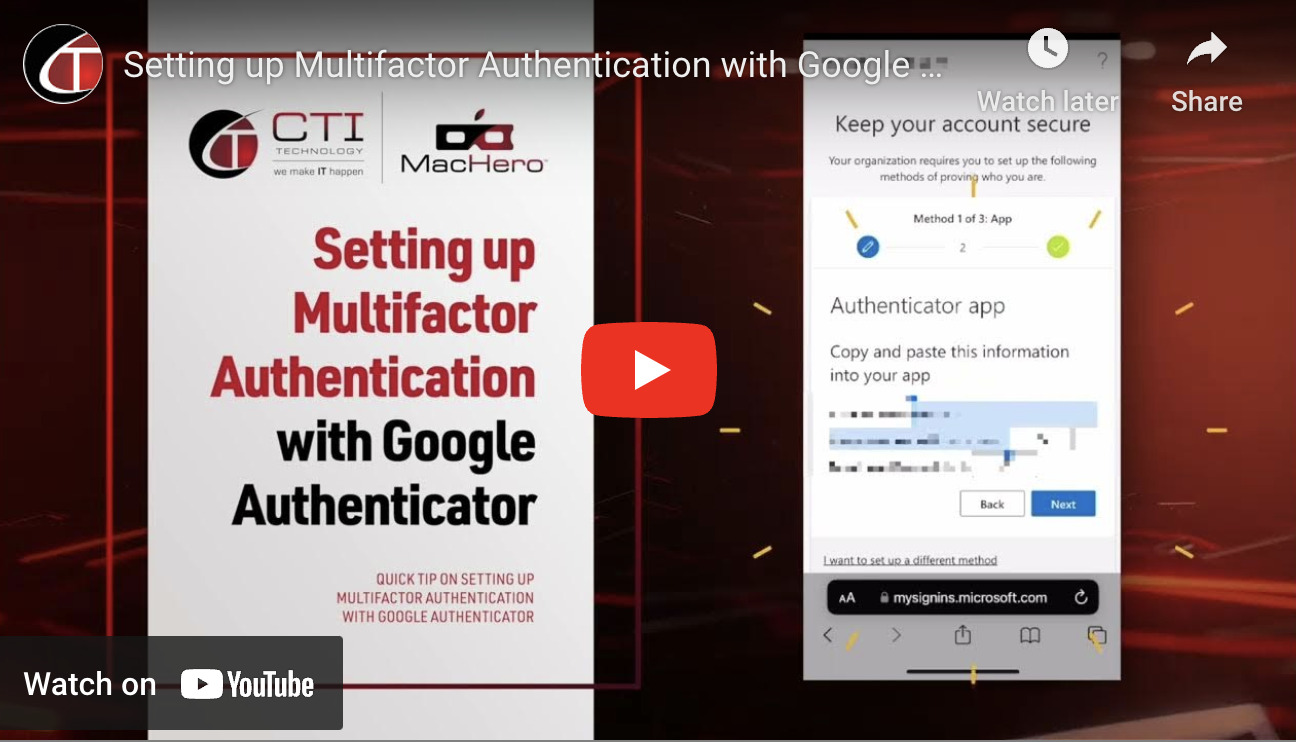

Setting up Multifactor Authentication with Google Authenticator for Microsoft 365
Enhance your Microsoft 365 security with Google Authenticator! Learn to set up Multi-Factor Authentication for added account protection. Safeguard your data effectively in this step-by-step[...]

Setting up Multifactor Authentication with SMS
Enhance Microsoft 365 security with SMS-based Multifactor Authentication. Our guide simplifies setup for added protection in the digital age. Learn how to configure and test[...]
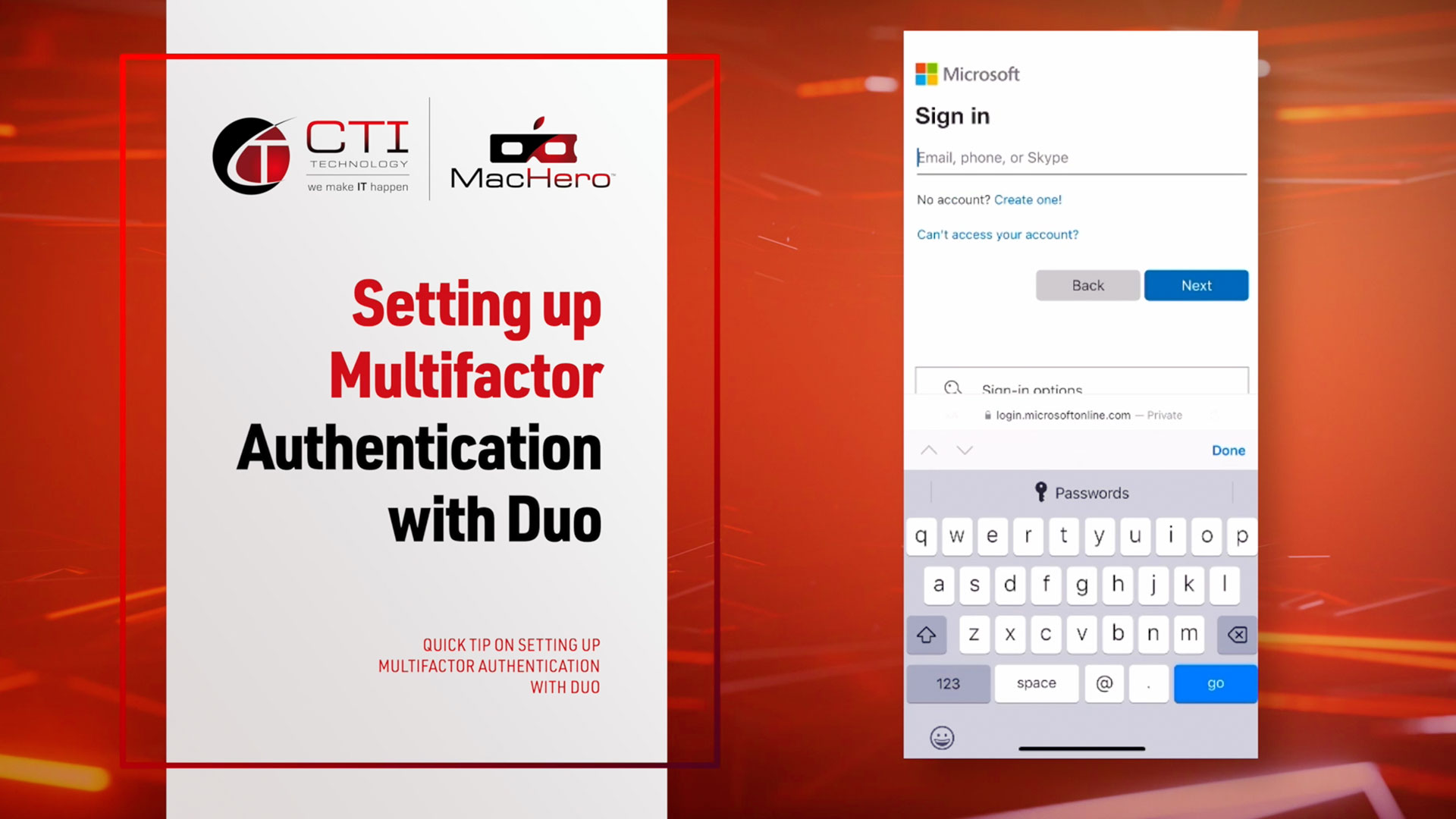

Setting Up Duo Two Factor Authentication with Microsoft 365
Enhance Microsoft 365 Security with Duo 2FA Setup | Learn How to Configure CTI Technology's Two-Factor Authentication for Ultimate Protection. Boost your Microsoft 365 account[...]


Assessing Your Organization’s Readiness Progress
Cybersecurity Awareness Month: Assessing Your Organization’s Readiness Progress As we reach the halfway point of Cybersecurity Awareness Month, it’s time to take a moment to[...]


Employees Ignore Cybersecurity Policies
Employees Ignore Cybersecurity Policies: Alarming Trends and Solutions In today’s digital era, cybersecurity is a primary concern for businesses across various industries. Organizations often put[...]

