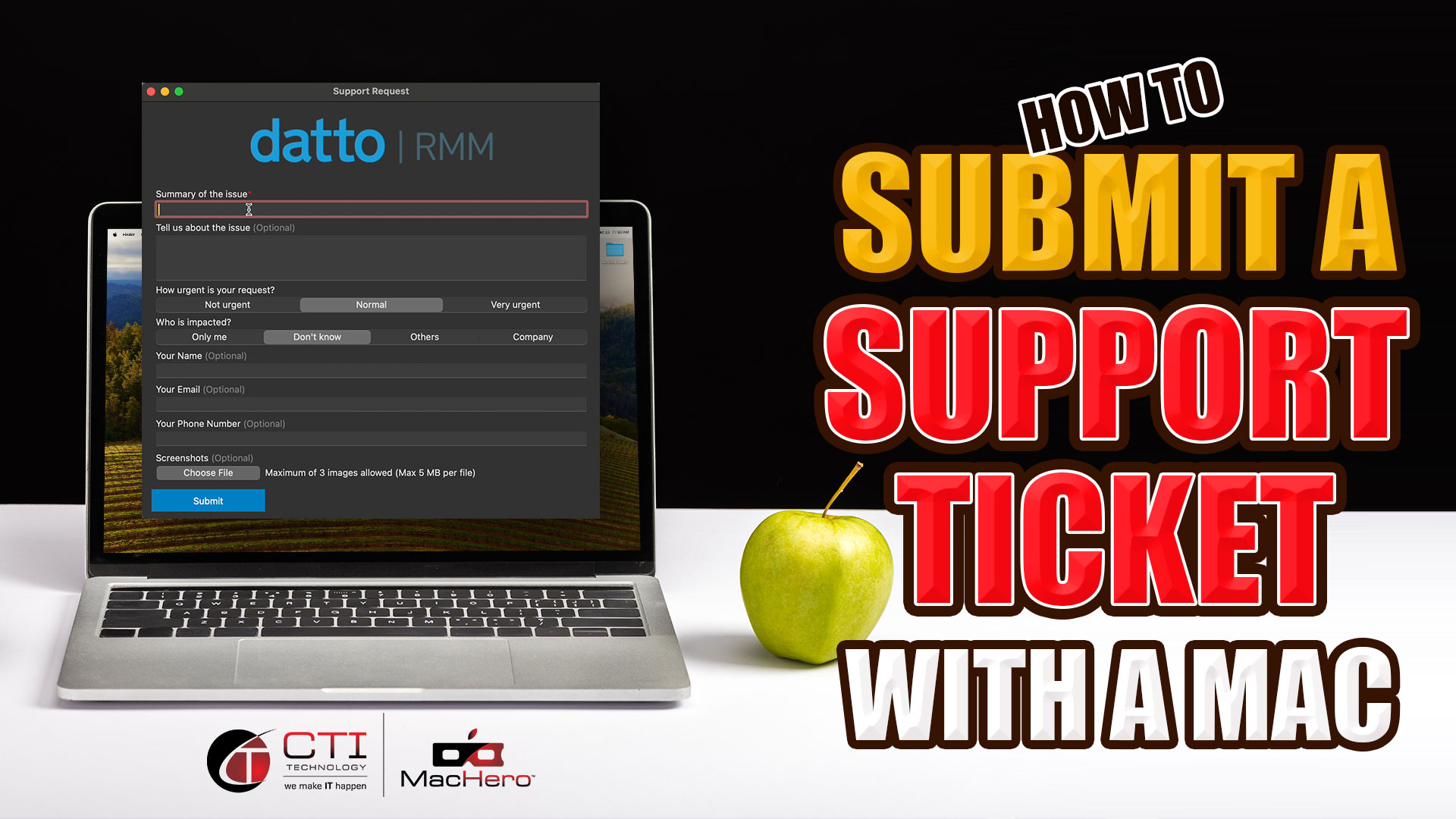
Social Engineering And The Impact On Business In Chicago
Social engineering has a massive bearing on the number of cyberattacks, however small, big, or sophisticated the attacks are. In fact, according to a recent study, 98% of cyberattacks depend on social engineering.
But what exactly is social engineering? Social engineering plays on your insecurities, greed, and fears to trick you into giving hackers your passwords, logins, and other sensitive information. It uses cognitive biases of the human brain to map a suitable attack technique. In a nutshell, social engineering is a malicious practice that manipulates people into disclosing their sensitive information by using the cognitive biases of the human brain.

Stages of a Social Engineering Attack
A social engineering attack is divided into four stages, as shown below:
- Research Stage: This stage involves the attacker gathering information about the victim’s personal and professional life, interests, and similar factors that have a significant bearing in determining the attack’s success rate. For instance, attackers may visit your social media page and try to connect with what you do and whom you do it with. They’ll learn about your relations with different people and how you communicate with them, the types of punctuations you use, the signature on your email, among other things. In essence, what the attackers are trying to do is gather a story that they can use to impersonate you to swindle the people with who you relate, such as clients, vendors, and employees.
- Engagement: The attacker then initiates a smooth conversation with the target without leaving any room for mistrust or doubt. For example, you may receive an email from an unknown individual saying that it was nice catching up with you and talking about the kids. The email will even go forward to ask you to send them a picture of the kids. Beware! This is how the hacking process begins.
- The Attack Stage: After creating a rapport with the target and engaging them adequately, the attackers then trick their targets into performing an action. For example, the attacker may contact their victims with a phony story such as losing their wallet and then asking that victim to send them some form of payment or credit card details.
- Closure: After successfully fulfilling their motive, the attacker will stop communicating with the victim. They do this while raising little or no suspicion.
Types of Social Engineering Techniques and Attacks
The key to protecting your organization from social engineering attacks is being alert and instituting an ongoing awareness program throughout your organization that educates your employees on how these attacks are carried out. Taking such measures will ensure that your employees can identify potential attack scenarios and keep away from them and report such cases to the IT department for remediation. Below are some common techniques used by hackers:
- Phishing: Phishing involves using a fake chat, website, or email to obtain sensitive information such as login credentials. Phishing attacks may convey messages from a bank or any other trusted entity asking you to verify your login credentials. Alternatively, hackers can convey an expertly designed message claiming that you are the winner of a substantial amount of money. Typically, the message is usually accompanied by a request for your banking details. Other phishing attacks even come in the form of pleas for charity following a calamity. Unfortunately, if you are naive, you may fall prey to these attacks.
- Baiting: This technique involves the attacker dangling something enticing to encourage their victim into taking a given action. Attackers use things like music or movie downloads to entice their victims. Upon downloading these files, the company or the individual’s computer is infected, thereby providing the criminal with a point of access to the victim’s files.
- Pretexting: Pretexting is where the attacker impersonates an authority figure or someone trusted to gain access to sensitive information such as login details. For instance, an attacker may present themselves as an investigator conducting company audits or an IT person purportedly needing to carry out system maintenance.
- Water holing: This social engineering technique entails attackers guessing or observing various websites that given organizations use frequently. The attackers then narrow down those familiar to employees of a given organization and infect them with malicious codes and Trojans.
- Tailgating: This is where the attacker tries to gain access to secure locations by manipulating the victim ( such as employees) into believing that they have the authority to access these locations. For instance, an attacker might request that you unlock the front door using an identity token. Alternatively, they may use an RFID tag to manipulate you into believing that they forgot their tag. Generally, tailgating takes advantage of customary courtesy.
Ways of Preventing Social Engineering Attacks
Below are some of the measures you can take to prevent social engineering attacks:
Training and awareness
Social engineering attacks mostly happen due to naivety and lack of attention. Providing your employees with proper training and regular awareness campaigns will make them well informed about how these attacks are carried out. They can therefore avoid taking actions that may jeopardize your company’s data.
Preventive protocols, tools, and policies
It’s crucial that you have the necessary software to insulate you from social engineering attacks. Software solutions such as firewalls, antivirus, anti-spyware, among others, can help you tighten loose ends, thereby enhancing the security of your system. Besides the security software, you should ensure that you put in place standard protocols and policies to further enhance your company’s ability to thwart social engineering attacks.
Develop a unified framework
Set up a standard framework that clearly outlines how people in your organization handle data. Moreover, you need to ensure that everyone in your organization is conversant with the protocols for sharing information internally and externally and the ways of dealing with suspicious emails, among other threats. Instituting this measure will ensure that your employees not only know how but when and with whom to share various information.
CTI Technology Can Help Protect Your Company From Social Engineering Attacks
Falling victim to social engineering attacks can have a far-reaching impact on your company, such as loss of sensitive data and incurring high costs. Don’t take chances; seek the services of CTI technology to help protect your Chicago-based company from social engineering and cybersecurity attacks. We offer a wide range of IT services including, fractional CIO/CTO, cybersecurity, and IT services and support. Contact us today and let us enhance your company’s security.
Why Is CTI Technology The Best Choice For IT Services In The Chicagoland Region?